Remote Desktop Service on Server 2008 R2 – Part4
RD Gateway
Technology review
RD Gateway uses the Remote Desktop Protocol (RDP) over HTTPS to help establish a secure, encrypted connection between remote users on the Internet and the internal network resources on which their productivity applications run.
To function correctly, RD Gateway requires several role services and features to be installed and running. When you use Server Manager to install the RD Gateway role service, the following additional roles, role services, and features are automatically installed and started, if they are not already installed:
- Remote procedure call (RPC) over HTTP Proxy
- Web Server (IIS) [Internet Information Services]
IIS must be installed and running for the RPC over HTTP Proxy feature to function. - Network Policy and Access Services
Step 2: Installing RD Gateway
Updated: June 24, 2009
Applies To: Windows 7, Windows Server 2008 R2
To install and configure an RD Gateway server, you must add the RD Gateway role service. Windows Server 2008 R2 includes the option to install the RD Gateway role service by using Server Manager. This topic covers the installation and configuration of the RD Gateway role service on the RDG-SRV computer in the CONTOSO domain.
Membership in the local Administrators group, or equivalent, on the RD Gateway server that you plan to configure, is the minimum required to complete this procedure. Review details about using the appropriate accounts and group memberships at Local and Domain Default Groups (http://go.microsoft.com/fwlink/?LinkId=83477).
To install the RD Gateway role service
-
Log on to RDG-SRV as CONTOSO\Administrator.
-
Open Server Manager. To open Server Manager, click Start, point to Administrative Tools, and then click Server Manager.
-
Under the Roles Summary heading, click Add Roles.
-
In the Add Roles Wizard, if the Before You Begin page appears, click Next.
-
On the Select Server Roles page, under roles, select the Remote Desktop Services check box, and then click Next.
-
On the Remote Desktop Services page, click Next.
-
On the Select Role Services page, select the Remote Desktop Gateway check box.
-
If prompted to specify whether you want to install the additional role services required for Remote Desktop Gateway, click Add Required Role Services.
-
On the Choose a Server Authentication Certificate for SSL Encryption page, select Create a self-signed certificate for SSL encryption, and then click Next.
-
On the Create Authorization Policies for RD Gateway page, select Now, and then click Next.
- On the Select User Groups That Can Connect Through RD Gateway page, click Add. In the Select Groups dialog box, specify Domain Users, and then click OK to close the Select Groups dialog box. Click Next.
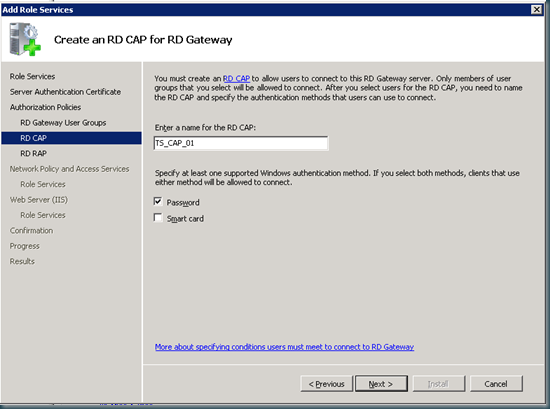
- On the Create an RD CAP for RD Gateway page, enter the name RD_CAP_01 for the Remote Desktop connection authorization policy (RD CAP), select Password, and then click Next.
- On the Create an RD RAP for RD Gateway page, enter the name RD_RAP_01 for the Remote Desktop resource authorization policy (RD RAP), and then select Allow users to connect to any computer on the network. Click Next.
- On the Select User Groups That Can Connect Through RD Gateway page, click Add. In the Select Groups dialog box, specify Domain Users, and then click OK to close the Select Groups dialog box. Click Next.
-
On the Network Policy and Access Services page (which appears if this role service is not already installed), review the summary information, and then click Next.
-
On the Select Role Services page, verify that Network Policy Server is selected, and then click Next.
-
On the Web Server (IIS) page (which appears if this role service is not already installed), review the summary information, and then click Next.
-
On the Select Role Services page, accept the default selections for Web Server (IIS), and then click Next.
-
On the Confirm Installation Selections page, verify that the following role services will be installed:
- Remote Desktop Services\RD Gateway
- Network Policy and Access Services\Network Policy Server
- Web Server (IIS)
- RPC over HTTP Proxy
-
On the Installation Progress page, installation progress will be noted.
-
On the Installation Results page, confirm that installation for these roles, role services, and features was successful, and then clickClose.
To export the SSL certificate for the RD Gateway server and copy it to the CONTOSO-CLNT computer
-
On the RD Gateway server, open the Certificates snap-in console. If you have not already added the Certificates snap-in console, you can do so by doing the following:
- Click Start, click Run, type mmc and then click OK.
- On the File menu, click Add/Remove Snap-in.
- In the Add or Remove Snap-ins dialog box, in the Available snap-ins list, click Certificates, and then click Add.
- In the Certificates snap-in dialog box, click Computer account, and then click Next.
- In the Select Computer dialog box, click Local computer: (the computer this console is running on), and then click Finish.
- In the Add or Remove snap-ins dialog box, click OK.
-
In the Certificates snap-in console, in the console tree, expand Certificates (Local Computer), expand Personal, and then clickCertificates.
-
Right-click the certificate RDG-SRV.contoso.com, point to All Tasks, and then click Export.
-
On the Welcome to the Certificate Export Wizard page, click Next.
-
On the Export Private Key page, click No, do not export private key, and then click Next.
-
On the Export File Format page, ensure that DER encoded binary X.509 (.CER) is selected, and then click Next.
-
On the File to Export page, in the File name box, click Browse.
-
In the Save As dialog box, in the File name box, enter RDG-SRV, and then click Save.
-
On the File to Export page, click Next.
-
On the Completing the Certificate Export Wizard page, confirm that the correct certificate is specified, that Export Keys is set toNo, and that Include all certificates in the certification path is set to No, and then click Finish.
-
After the certificate export has successfully completed, a message appears confirming that the export was successful. Click OK.
-
Close the Certificates snap-in.
-
Copy the RD Gateway server certificate c:\users\administrator.CONTOSO\Documents\RDG-SRV.cer, to the CONTOSO-CLNT computer.
To verify the functionality of the RD Gateway deployment, complete the following:
- Install the SSL certificate for the RD Gateway server on the CONTOSO-CLNT computer.
- Enable certificate revocation checking on the CONTOSO-CLNT computer. (Optional)
- Log on to CONTOSO-CLNT as Morgan Skinner and use Remote Desktop Connection (RDC) to connect to the RD Session Host server (RDSH-SRV) by using the RD Gateway server (RDG-SRV).
To install the SSL certificate for the RD Gateway server on the CONTOSO-CLNT computer
-
Log on to CONTOSO-CLNT as CONTOSO\Administrator.
-
Open the Certificates snap-in console by doing the following:
- Click Start, click Run, type mmc and then click OK.
- On the File menu, click Add/Remove Snap-in.
- In the Add or Remove Snap-ins dialog box, in the Available snap-ins list, click Certificates, and then click Add.
- In the Certificates snap-in dialog box, click Computer account, and then click Next.
- In the Select Computer dialog box, click Local computer: (the computer this console is running on), and then click Finish.
- In the Add or Remove snap-ins dialog box, click OK.
-
In the Certificates snap-in console, in the console tree, expand Certificates (Local Computer), and then click Trusted Root Certification Authorities.
-
Right-click the Trusted Root Certification Authorities folder, point to All Tasks, and then click Import.
-
On the Welcome to the Certificate Import Wizard page, click Next.
-
On the File to Import page, in the File name box, click Browse, and then browse to the location where you copied the SSL certificate for the RD Gateway server. From the file type drop-down list, select All Files (*.*). Select the certificate RDG-SRV.cer, click Open, and then click Next.
-
On the Certificate Store page, accept the default option (Place all certificates in the following store - Trusted Root Certification Authorities), and then click Next.
-
On the Completing the Certificate Import Wizard page, confirm that the correct certificate has been selected and that the following certificate settings appear:
- Certificate Store Selected by User: Trusted Root Certification Authorities
- Content: Certificate
- File Name: FilePath\RDG-SRV.cer
-
Click Finish.
-
After the certificate import has successfully completed, a message appears confirming that the import was successful. Click OK.
-
With Certificates selected in the console tree, in the details pane, verify that the correct certificate appears in the list of certificates on the CONTOSO-CLNT computer.
-
Log off from the CONTOSO-CLNT computer.
To enable certificate revocation checking on the CONTOSO-CLNT computer (Optional)
-
Log on to CONTOSO-CLNT as CONTOSO\Administrator.
-
Click Start, point to All Programs, and then click Accessories.
-
Right-click Command Prompt, and then click Run as administrator.
-
If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Yes.
-
At the command prompt, type
reg add "HKCU\Software\Microsoft\Terminal Server Gateway\Transports\Rpc" /v CheckForRevocation /t REG_DWORD /d 1..gif) Warning
WarningThe publishing and maintenance of the certificate revocation list is an integral part of the public key infrastructure (PKI) and is external to RD Gateway. Please do not enable certificate revocation checking on RD Gateway clients until you have confirmed that your deployment can support this; otherwise, even the basic connection to an end resource through the RD Gateway server will not work. This is the reason why certificate revocation checking is disabled by default on the RD Gateway client, and the recommendation is to turn it on as a security best practice only after ensuring that the certificate revocation list is accessible from the Internet.
-
Log off the computer.
To connect to RDSH-SRV with RDC by using RDG-SRV
-
Log on to CONTOSO-CLNT as Morgan Skinner.
-
Click Start, point to All Programs, point to Accessories, and then click Remote Desktop Connection.
-
In the Remote Desktop Connection dialog box, click Options.
-
On the Advanced tab, click Settings.
-
On the RD Gateway Server Settings page, click Use these RD Gateway server settings, enter the following settings, and then click OK.
-
On the General tab, in the Computer box, type rdsh-srv, and then click Connect.
-
In the Windows Security dialog box, type the password for contoso\mskinner, and then click OK.
-
If the connection is successful, a Windows desktop will appear on the screen for RDSH-SRV.
You have successfully deployed and demonstrated the functionality of RD Gateway on Remote Desktop Services by using the simple scenario of connecting to an RD Session Host server by using RD Gateway with an authorized remote user account by using Remote Desktop Connection. You can also use this deployment to explore some of the additional capabilities of Remote Desktop Services through additional configuration and testing.















Comments
Post a Comment