Remote Desktop Service on Server 2008 R2 – Part3
RD Web Access
eploying Remote Desktop Web Access with Remote Desktop Connection Broker Step-by-Step Guide
Updated: October 12, 2010
Applies To: Windows 7, Windows Server 2008 R2
About this guide
RemoteApp and Desktop Connection allows administrators to provide a set of resources, such as RemoteApp programs and virtual desktops, to their users. Users can connect to RemoteApp and Desktop Connection in two ways:
- From a computer running Windows® 7. When set up, resources that are part of RemoteApp and Desktop Connection appear in the Start menu under All Programs in a folder called RemoteApp and Desktop Connections.
- From a Web browser by signing in to the website that is provided by RD Web Access. In this case, a computer that is running Windows 7 is not required.
This step-by-step guide walks you through the process of setting up a working RemoteApp source that is accessible by using Remote Desktop Web Access (RD Web Access). During this process, you will deploy the following components in a test environment:
- A Remote Desktop Connection Broker (RD Connection Broker) server
- A Remote Desktop Web Access (RD Web Access) server
This guide also explains how to configure Single Sign On so that users are only prompted once for credentials. When you deploy Single Sign On, consider the following certificate requirements:
- The certificate must be trusted explicitly or from a trusted root certificate.
- The certificate name or the Subject Alternative Name must match the fully-qualified domain name of the server.
- The certificate must support Server Authentication or Remote Desktop Authentication Extended Key Usage.
- Indirect certificate revocation lists are not supported.
- Certificate revocation checks are performed by default.
- When you use CredSSP, you can turn off certificate revocation checks by configuring the following registry entry to a value of 1: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Credssp\UseCachedCRLOnlyAndIgnoreRevocationUnknownErrors
- When you use Transport Layer Security (TLS), you can turn off certificate revocation checks by configuring the following registry entries to a value of 0: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Terminal Server Client\ CertChainRevocationCheck and HKEY_CURRENT_USER\SOFTWARE\Microsoft\Terminal Server Client\ CertChainRevocationCheck
==============================================================
Configure the RD Session Host server (RDSH-SRV)
To configure the server RDSH-SRV, you must:
- Configure a certificate used to digitally sign the RDP file.
- Add the thumbprint of the certificate used to digitally sign the RDP file to the Default Domain Group Policy setting by using the Group Policy Management Console (GPMC).
First, configure a certificate used to digitally sign the RDP file by using RemoteApp Manager. This procedure assumes that you have already imported a certificate into the Personal certificate store of the computer account.
To configure a certificate used to digitally sign the RDP file
-
Log on to RDSH-SRV as CONTOSO\Administrator.
-
Click Start, point to Administrative Tools, point to Remote Desktop Services, and then click RemoteApp Manager.
-
Under the Overview section, click Change next to Digital Signature Settings.
-
Select the Sign with a digital certificate check box.
-
Click Change.
-
On the Confirm Certificate page, select the appropriate certificate, and then click OK.
-
Click OK to close the RemoteApp Deployment Settings dialog box.
Finally, you must add the thumbprint of the certificate used to digitally sign the RDP file to the Default Domain Group Policy setting. This is required so that the trusted publisher warning dialog box is not shown to the user each time the RemoteApp program is started.
To add the certificate thumbprint to the Default Domain Group Policy setting
-
Log on to CONTOSO-DC as CONTOSO\Administrator.
-
Open the GPMC. To open the GPMC, click Start, point to Administrative Tools, and then click Group Policy Management.
-
Expand Forest: contoso.com, expand Domains, and then expand contoso.com.
-
Right-click Default Domain Policy, and then click Edit.
-
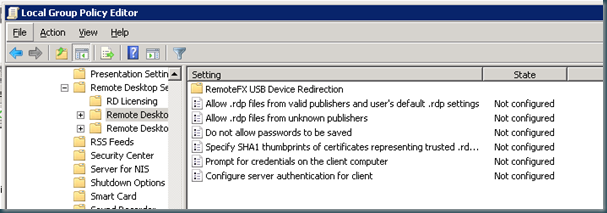
Navigate to Computer Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Connection Client.
-
Double-click Specify SHA1 thumbprints of certificates representing trusted .rdp publishers.
-
Select the Enabled option.
-
In the Comma-separated list of SHA1 trusted certificate thumbprints box, type the certificate thumbprint used to digitally sign the RDP file, and then click OK.
Configure the client computer (CONTOSO-CLNT)
To configure the client computer CONTOSO-CLNT, you must:
- Import the digital certificate used by RDSH-SRV to the Trusted Root Certification Authorities certificate store of the computer account.
Import the digital certificate used by RDSH-SRV to the Trusted Root Certification Authorities certificate store of the computer account on CONTOSO-CLNT.
To import a digital certificate to the Trusted Root Certification Authorities certificate store
-
Log on to CONTOSO-CLNT as CONTOSO\Administrator.
-
Click Start, and then click Run.
-
Type mmc and then click OK.
-
Click File, and then click Add/Remove Snap-in.
-
In the Available snap-ins box, click Certificates, and then click Add.
-
Select the Computer account option, click Next, and then click Finish.
-
Click OK.
-
Expand Certificates (Local Computer).
-
Right-click Trusted Root Certification Authorities, point to All Tasks, and then click Import.
-
On the Welcome to the Certificate Import Wizard page, click Next.
-
Click Browse.
-
Click Personal Information Exchange (*.pfx, *.p12) to filter the file results to show only PFX and P12 files.
.gif) Important
ImportantYou must import a PFX certificate file that includes the private key.
-
Navigate to the folder where the certificate is located, click the certificate, and the click Open.
-
Click Next.
-
In the Password box, type the password for the PFX file, and then click Next.
-
Click Next, and then click Finish.
Configure the RD Web Access server (RDWA-SRV)
To configure the RD Web Access server by using Windows Server 2008 R2, you must:
- Install Windows Server 2008 R2.
- Configure TCP/IP properties.
- Join RDWA-SRV to the contoso.com domain.
- Install the RD Web Access role service.
- Add the thumbprint of the certificate used for the RD Web Access server to the Default Domain Group Policy setting by using the GPMC.
Next, install the RD Web Access role service by using Server Manager.
To install the RD Web Access role service
-
Log on to RDWA-SRV as CONTOSO\Administrator.
-
Click Start, point to Administrative Tools, and then click Server Manager.
-
Under the Roles Summary heading, click Add Roles.
-
On the Before You Begin page, click Next.
-
On the Select Server Roles page, select the Remote Desktop Services check box, and then click Next.
-
On the Remote Desktop Services page, click Next.
-
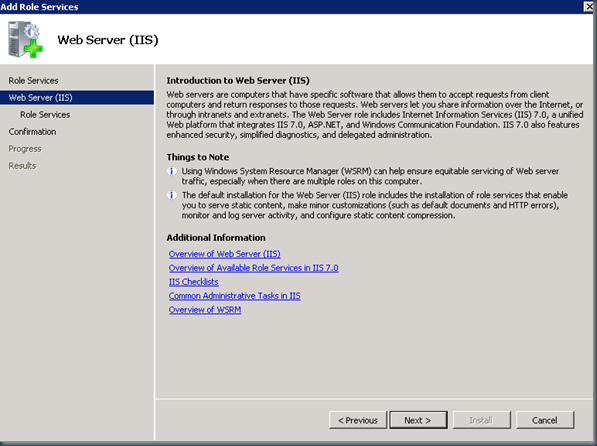
On the Select Role Services page, select the Remote Desktop Web Access check box.
-
Review the information about adding Web Server (IIS) and the Remote Server Administration Tools, click Add Required Role Services, and then click Next.
Finally, you must add the thumbprint of the RD Web Access server certificate to the Default Domain Group Policy setting. This is required so that the trusted publisher warning dialog box is not shown to the user each time the RemoteApp program is started.
To add the certificate thumbprint to the Default Domain Group Policy setting
-
Log on to CONTOSO-DC as CONTOSO\Administrator.
-
Open GPMC. To open GPMC, click Start, point to Administrative Tools, and then click Group Policy Management.
-
Expand Forest: contoso.com, expand Domains, and then expand contoso.com.
-
Right-click Default Domain Policy, and then click Edit.
-
Navigate to Computer Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Connection Client.
-
Double-click Specify SHA1 thumbprints of certificates representing trusted .rdp publishers.
-
Select the Enabled option.
-
In the Comma-separated list of SHA1 trusted certificate thumbprints box, type the certificate thumbprint used to digitally sign the RDP file, and then click OK.
You have set up the CONTOSO domain. Now you can proceed to Step 2: Installing and Configuring RemoteApp.
==============================================================
Next, assign a RemoteApp source on the RD Web Access server (RDWA-SRV).
To assign a RemoteApp source on RDWA-SRV
-
Log on to RDWA-SRV as CONTOSO\Administrator.
-
Click Start, point to Administrative Tools, point to Remote Desktop Services, and then click Remote Desktop Web Access Configuration.
-
Click Continue to this website (not recommended).
.gif) Important
ImportantThis guide uses a self-signed certificate for the RD Web Access server. Self-signed certificates are not recommended in a production environment. You should use a certificate that is trusted from a certification provider when deploying RD Web Access in a production environment.
-
In the Domain\user name box, type CONTOSO\Administrator.
-
In the Password box, type the password that you specified for CONTOSO\Administrator, and then click Sign in.
-
On the Configuration page, click An RD Connection Broker server.
Finally, you must add a RemoteApp source on the RDCB-SRV computer by using Remote Desktop Connection Manager.
To add a RemoteApp source by using Remote Desktop Connection Manager
-
Log on to RDCB-SRV as CONTOSO\Administrator.
-
Click Start, point to Administrative Tools, point to Remote Desktop Services, and then click Remote Desktop Connection Manager.
-
Click RemoteApp Sources, and then in the Actions pane, click Add RemoteApp Source.
-
In the RemoteApp source name box, type rdsh-srv and then click Add.
==============================================================
==============================================================
Step 3: Verifying RemoteApp Functionality
Updated: October 12, 2010
Applies To: Windows 7, Windows Server 2008 R2
To verify the functionality of a RemoteApp program deployment, log on as Morgan Skinner and connect to the RemoteApp program by using Remote Desktop Web Access (RD Web Access).
To connect to the RemoteApp program
-
Log on to CONTOSO-CLNT as Morgan Skinner (CONTOSO\mskinner).
-
Click Start, point to All Programs, and then click Internet Explorer.
-
In the Address bar, type https://rdwa-srv.contoso.com/RDWeb and then press ENTER.
-
Click Continue to this website (not recommended).
.gif) Important
ImportantThis guide uses a self-signed certificate for the RD Web Access server. Self-signed certificates are not recommended in a production environment. You should use a certificate that is trusted from a certification provider when deploying RD Web Access in a production environment.
-
In the Domain\user name box, type CONTOSO\mskinner.
-
In the Password box, type the password that you specified for Morgan Skinner, and then click Sign in.
.gif) Note
NoteIn you receive a prompt asking you to install the Microsoft Remote Desktop Services Web Access Control, clickRun Add-on, and then click Run.
-
Click Calculator, and then click Connect.
-
When prompted, enter the credentials for Morgan Skinner, and then click OK.
You have successfully deployed and demonstrated the functionality of a RemoteApp program by using the simple scenario of connecting to Calculator by using RD Web Access. You can also use this deployment to explore some of the additional capabilities of personal virtual desktops through additional configuration and testing.













Comments
Post a Comment