Ticket: RemoteAPP certificate revocation check error
certutil -f –urlfetch -verify <your_certificate>.cer
From internet client (Win7 ultimate x64)
Issuer:
CN=TWCA Secure CA -Evaluation Only
OU=SSL Certification Service Provider-Evaluation Only
O=TAIWAN-CA INC.
C=TW
Subject:
CN=deep2.msft.com
OU=ITS
O=Msft Corporation
L=Taipei
S=Taiwan
C=TW
Cert Serial Number: 04bd
dwFlags = CA_VERIFY_FLAGS_ALLOW_UNTRUSTED_ROOT (0x1)
dwFlags = CA_VERIFY_FLAGS_IGNORE_OFFLINE (0x2)
dwFlags = CA_VERIFY_FLAGS_FULL_CHAIN_REVOCATION (0x8)
dwFlags = CA_VERIFY_FLAGS_CONSOLE_TRACE (0x20000000)
dwFlags = CA_VERIFY_FLAGS_DUMP_CHAIN (0x40000000)
ChainFlags = CERT_CHAIN_REVOCATION_CHECK_CHAIN (0x20000000)
HCCE_LOCAL_MACHINE
CERT_CHAIN_POLICY_BASE
-------- CERT_CHAIN_CONTEXT --------
ChainContext.dwErrorStatus = CERT_TRUST_REVOCATION_STATUS_UNKNOWN (0x40)
ChainContext.dwErrorStatus = CERT_TRUST_IS_OFFLINE_REVOCATION (0x1000000)
ChainContext.dwErrorStatus = CERT_TRUST_IS_PARTIAL_CHAIN (0x10000)
SimpleChain.dwErrorStatus = CERT_TRUST_REVOCATION_STATUS_UNKNOWN (0x40)
SimpleChain.dwErrorStatus = CERT_TRUST_IS_OFFLINE_REVOCATION (0x1000000)
SimpleChain.dwErrorStatus = CERT_TRUST_IS_PARTIAL_CHAIN (0x10000)
CertContext[0][0]: dwInfoStatus=2 dwErrorStatus=1000040
Issuer: CN=TWCA Secure CA -Evaluation Only, OU=SSL Certification Service Provider-Evaluation Only, O=TAIWAN-CA INC., C=TW
NotBefore: 6/20/2011 2:03 PM
NotAfter: 7/19/2011 11:59 PM
Subject: CN=deep2.msft.com, OU=ITS, O=Msft Corporation, L=Taipei, S=Taiwan, C=TW
Serial: 04bd
bb 06 52 a5 52 b1 62 b4 8d 2c e4 e3 75 56 a1 10 d4 61 c7 95
Element.dwInfoStatus = CERT_TRUST_HAS_KEY_MATCH_ISSUER (0x2)
Element.dwErrorStatus = CERT_TRUST_REVOCATION_STATUS_UNKNOWN (0x40)
Element.dwErrorStatus = CERT_TRUST_IS_OFFLINE_REVOCATION (0x1000000)
---------------- Certificate AIA ----------------
No URLs "None" Time: 0
---------------- Certificate CDP ----------------
OK "Base CRL (099c)" Time: 0
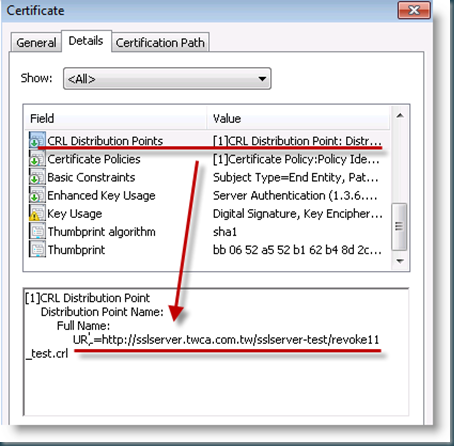
[0.0] http://sslserver.twca.com.tw/sslserver-test/revoke11_test.crl
---------------- Certificate OCSP ----------------
No URLs "None" Time: 0
--------------------------------
Issuance[0] = 2.16.886.3.1.3.999
Application[0] = 1.3.6.1.5.5.7.3.1 Server Authentication
Application[1] = 1.3.6.1.5.5.7.3.2 Client Authentication
Exclude leaf cert:
da 39 a3 ee 5e 6b 4b 0d 32 55 bf ef 95 60 18 90 af d8 07 09
Full chain:
bb 06 52 a5 52 b1 62 b4 8d 2c e4 e3 75 56 a1 10 d4 61 c7 95
Missing Issuer: CN=TWCA Secure CA -Evaluation Only, OU=SSL Certification Service Provider-Evaluation Only, O=TAIWAN-CA INC., C=TW
Issuer: CN=TWCA Secure CA -Evaluation Only, OU=SSL Certification Service Provider-Evaluation Only, O=TAIWAN-CA INC., C=TW
NotBefore: 6/20/2011 2:03 PM
NotAfter: 7/19/2011 11:59 PM
Subject: CN=deep2.msft.com, OU=ITS, O=Msft Corporation, L=Taipei, S=Taiwan, C=TW
Serial: 04bd
bb 06 52 a5 52 b1 62 b4 8d 2c e4 e3 75 56 a1 10 d4 61 c7 95
A certificate chain could not be built to a trusted root authority. 0x800b010a (-2146762486)
------------------------------------
Incomplete certificate chain
Cannot find certificate:
CN=TWCA Secure CA -Evaluation Only, OU=SSL Certification Service Provider-Evaluation Only, O=TAIWAN-CA INC., C=TW
Cert is an End Entity certificate
ERROR: Verifying leaf certificate revocation status returned The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613)
CertUtil: The revocation function was unable to check revocation because the revocation server was offline.
CertUtil: -verify command completed successfully.
=====================================================
Another result from Remote Desktop server with Trusted root & Intermediate Certification Athorities
Issuer:
CN=TWCA Secure CA -Evaluation Only
OU=SSL Certification Service Provider-Evaluation Only
O=TAIWAN-CA INC.
C=TW
Subject:
CN=deep2.msft.com
OU=ITS
O=msft Corporation
L=Taipei
S=Taiwan
C=TW
Cert Serial Number: 04bd
dwFlags = CA_VERIFY_FLAGS_ALLOW_UNTRUSTED_ROOT (0x1)
dwFlags = CA_VERIFY_FLAGS_IGNORE_OFFLINE (0x2)
dwFlags = CA_VERIFY_FLAGS_FULL_CHAIN_REVOCATION (0x8)
dwFlags = CA_VERIFY_FLAGS_CONSOLE_TRACE (0x20000000)
dwFlags = CA_VERIFY_FLAGS_DUMP_CHAIN (0x40000000)
ChainFlags = CERT_CHAIN_REVOCATION_CHECK_CHAIN (0x20000000)
HCCE_LOCAL_MACHINE
CERT_CHAIN_POLICY_BASE
-------- CERT_CHAIN_CONTEXT --------
ChainContext.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
SimpleChain.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
CertContext[0][0]: dwInfoStatus=102 dwErrorStatus=0
Issuer: CN=TWCA Secure CA -Evaluation Only, OU=SSL Certification Service Provider-Evaluation Only, O=TAIWAN-CA INC., C=TW
NotBefore: 6/20/2011 2:03 PM
NotAfter: 7/19/2011 11:59 PM
Subject: CN=deep2.msft.com, OU=ITS, O=msft Corporation, L=Taipei, S=Taiwan, C=TW
Serial: 04bd
bb 06 52 a5 52 b1 62 b4 8d 2c e4 e3 75 56 a1 10 d4 61 c7 95
Element.dwInfoStatus = CERT_TRUST_HAS_KEY_MATCH_ISSUER (0x2)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
---------------- Certificate AIA ----------------
No URLs "None" Time: 0
---------------- Certificate CDP ----------------
Verified "Base CRL (099c)" Time: 0
[0.0] http://sslserver.twca.com.tw/sslserver-test/revoke11_test.crl
---------------- Base CRL CDP ----------------
No URLs "None" Time: 0
---------------- Certificate OCSP ----------------
No URLs "None" Time: 0
--------------------------------
CRL 099a:
Issuer: CN=TWCA Secure CA -Evaluation Only, OU=SSL Certification Service Provider-Evaluation Only, O=TAIWAN-CA INC., C=TW
e0 b8 a7 68 72 d9 7f b7 5a 04 90 c0 ae b0 f4 bb 0e 79 7d 35
Application[0] = 1.3.6.1.5.5.7.3.1 Server Authentication
CertContext[0][1]: dwInfoStatus=102 dwErrorStatus=0
Issuer: CN=Baltimore CyberTrust Root, OU=CyberTrust, O=Baltimore, C=IE
NotBefore: 12/9/2010 1:49 AM
NotAfter: 10/1/2016 12:47 AM
Subject: CN=TWCA Secure CA -Evaluation Only, OU=SSL Certification Service Provider-Evaluation Only, O=TAIWAN-CA INC., C=TW
Serial: 072744b8
23 f2 70 6a 7f 72 ce 49 73 9c fb e1 fa ae c5 ad fc a3 64 97
Element.dwInfoStatus = CERT_TRUST_HAS_KEY_MATCH_ISSUER (0x2)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
---------------- Certificate AIA ----------------
No URLs "None" Time: 0
---------------- Certificate CDP ----------------
Verified "Base CRL (a2)" Time: 11
[0.0] http://cdp1.public-trust.com/CRL/Omniroot2025.crl
---------------- Base CRL CDP ----------------
No URLs "None" Time: 0
---------------- Certificate OCSP ----------------
No URLs "None" Time: 0
--------------------------------
CRL a2:
Issuer: CN=Baltimore CyberTrust Root, OU=CyberTrust, O=Baltimore, C=IE
e3 19 28 54 52 08 45 e0 2f 8a 76 3f 58 d2 bc 95 f9 20 be dd
Issuance[0] = 1.3.6.1.4.1.6334.1.0
Application[0] = 1.3.6.1.5.5.7.3.1 Server Authentication
Application[1] = 1.3.6.1.5.5.7.3.4 Secure Email
CertContext[0][2]: dwInfoStatus=10c dwErrorStatus=0
Issuer: CN=Baltimore CyberTrust Root, OU=CyberTrust, O=Baltimore, C=IE
NotBefore: 5/13/2000 2:46 AM
NotAfter: 5/13/2025 7:59 AM
Subject: CN=Baltimore CyberTrust Root, OU=CyberTrust, O=Baltimore, C=IE
Serial: 020000b9
d4 de 20 d0 5e 66 fc 53 fe 1a 50 88 2c 78 db 28 52 ca e4 74
Element.dwInfoStatus = CERT_TRUST_HAS_NAME_MATCH_ISSUER (0x4)
Element.dwInfoStatus = CERT_TRUST_IS_SELF_SIGNED (0x8)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
---------------- Certificate AIA ----------------
No URLs "None" Time: 0
---------------- Certificate CDP ----------------
No URLs "None" Time: 0
---------------- Certificate OCSP ----------------
No URLs "None" Time: 0
--------------------------------
Application[0] = 1.3.6.1.5.5.7.3.1 Server Authentication
Application[1] = 1.3.6.1.5.5.7.3.4 Secure Email
Exclude leaf cert:
5f 6d 29 1d d5 15 be a1 ce e4 ff 97 7b 60 33 1b 49 41 64 63
Full chain:
ed ab 08 78 02 67 e4 57 65 13 f0 38 43 e5 a0 4e e9 04 09 26
------------------------------------
Verified Issuance Policies: None
Verified Application Policies:
1.3.6.1.5.5.7.3.1 Server Authentication
Cert is an End Entity certificate
Leaf certificate revocation check passed
CertUtil: -verify command completed successfully.
========================================================
KB931125:根憑證更新 [2011 年 3 月]
http://www.microsoft.com/downloads/details.aspx?FamilyID=3a027078-4cd7-4b27-9837-3d7e58dd5a89&displayLang=zh-tw
更新根憑證
此功能的作用
更新根憑證功能會連絡線上 Windows Update 服務,查看 Microsoft 是否已新增憑證授權單位至其信任授權單位清單,不過只有在程式提出由非直接受信任的憑證授權單位 (未儲存在電腦信任憑證清單中的憑證) 所發出的憑證時才會進行。 如果憑證授權單位已新增至 Microsoft 的信任授權單位清單中,則該憑證授權單位的憑證將會自動新增至電腦上的信任憑證清單中。
收集、處理或傳輸的資訊
更新根憑證會將要求傳送到線上 Windows Update 服務,要求取得 Microsoft 根憑證計劃目前的根憑證授權單位清單。 如果清單中列出不受信任的憑證,更新根憑證會從 Windows Update 取得該憑證,並將其放在電腦上的信任憑證存放區中。 所傳輸的資訊包括根憑證的名稱和密碼編譯雜湊。Microsoft 不會使用此資訊來識別您的身分或連絡您。
如需 Windows Update 和隱私權的詳細資訊,請參閱 Update Services 隱私權聲明。
使用資訊
Microsoft 會用這些資訊更新電腦上的信任憑證清單。
選擇與控制
更新根憑證預設是啟用的。 系統管理員可以設定「群組原則」來停用電腦上的更新根憑證功能。
其他資訊
如果您提交了一份由未直接信任的根授權單位所發出的憑證,而且電腦上並未安裝更新根憑證元件,此時您將無法完成驗證所需的動作。 例如,您可能無法安裝軟體、檢視已加密或以數位簽署的電子郵件訊息,或使用瀏覽器來進行加密的工作階段。
================================================
How to refresh the CRL cache on Windows Vista
http://blogs.technet.com/b/pki/archive/2007/09/13/how-to-refresh-the-crl-cache-on-windows-vista.aspx
Certutil –urlcache crl
Certutil –getreg chain\chaincacheresyncfiletime
certutil -setreg chain\ChainCacheResyncFiletime @now
================================================
Remote Server Administration Tools for Windows 7 with Service Pack 1 (SP1)
http://www.microsoft.com/downloads/en/details.aspx?FamilyID=7d2f6ad7-656b-4313-a005-4e344e43997d
===============================================
Manual update CRL on Windows 7 client, failed
============================================
Final solution
http://social.technet.microsoft.com/Forums/en-US/winserverTS/thread/42556711-dba6-4b95-9417-a129f94d0758
http://support.microsoft.com/kb/2203302/en-us
Consider the following scenario:
- You have a computer that is running Windows 7, Windows Server 2008 R2, Windows Vista or Windows Server 2008.
- You try to establish a Remote Desktop Protocol (RDP) connection to a terminal server on this computer.
- The RDP connection is configured to use Secure Socket Layer (SSL) authentication and Credential Security Support Provider protocol (CredSSP).
In this scenario, the RDP connection fails.
Notes
- This issue occurs when the server certificate on the terminal server is issued by an intermediate certification authority (CA) without the authority information access extension.
- In Windows 7 and Windows Server 2008 R2, the "Terminal Services" is renamed as "Remote Desktop Services."
The CredSSP protocol does not provide the certificate chain information that is embedded in the server certificate. This problem occurs if the following two conditions are true:
- The server certificate is issued by an intermediate CA that is embedded in the root CA.
- The server certificate does not contain authority information access extensions that enable dynamic download of the chain information.
In this situation, the CertGetCertificateChain function cannot retrieve the full certificate chain of the server certificate. Therefore, the RDP connection fails.
================================================
Disable-WSManCredSSP
http://technet.microsoft.com/en-us/library/dd819469.aspx
C:\PS>Disable-WSManCredSSP -Role Server












 Back to the top
Back to the top


Comments
Post a Comment